Maritime cyber risk alludes to a proportion of the degree to which an innovation resource could be a potential circumstance or event, which might bring about transportation-related operations, safety, or security failures because of data or frameworks being corrupted, lost or compromised.
Cyberattacks on overall port offices have featured the critical requirement for port facility security officers (PFSOs) to redesign their network safety information and abilities.
According to IMO (International Maritime Organization), the Maritime Safety Committee, at its 98th session in June 2017, also adopted Resolution MSC.428(98) – Maritime Cyber Risk Management in Safety Management Systems. The resolution encourages administrations to ensure that cyber risks are appropriately addressed in existing safety management systems (as defined in the ISM Code) no later than the first annual verification of the company’s Document of Compliance after 1 January 2021.
Recently, some port communities have taken key first steps to drive cyber security capability development in their environments by engaging with investors and experts. For example, cyber security efforts are rapidly strengthening at key port trade hubs as a direct result of a new wave of investment accelerators, technical centers of excellence, and academic programs focused on innovative technologies, including start-ups in ports and maritime trade logistics.
Cybertechnologies have become essential to the operation and management of numerous systems critical to the safety and security of shipping and protection of the marine environment. In some cases, these systems are to comply with international standards and Flag Administration requirements. However, the vulnerabilities created by accessing, interconnecting, or networking these systems can lead to cyber risks which should be addressed. Vulnerable systems could include, but are not limited to:
- Bridge systems
- Cargo handling and management systems
- Propulsion and machinery management and power control systems
- Access control systems
- Passenger servicing and management systems
- Passenger facing public networks
- Administrative and crew welfare systems and
- Communication systems
Also, Cyber incidents can arise as the result of:
- A cyber security incident, which affects the availability and integrity of OT, for example corruption of chart data held in an Electronic Chart Display and Information System (ECDIS).
- An unintended system failure occurring during software maintenance and patching, for example using an infected USB drive to complete the maintenance.
- Loss of or manipulation of external sensor data, critical for the operation of a ship. This includes but is not limited to Global Navigation Satellite Systems (GNSS), of which the Global Positioning System (GPS) is the most frequently used.
- Failure of a system due to software crashes and/or “bugs”.
- Crew interaction with phishing attempts, which is the most common attack vector by threat actors, which could lead to the loss of sensitive data and the introduction of malware to shipboard systems.
Perceiving that no two associations in the transportation business are something similar, these Guidelines are communicated in expansive terms to have a far-reaching application. Ships with restricted digital related frameworks might track down a basic use of these Guidelines to be adequate; in any case, ships with complex digital related frameworks might require a more prominent degree of care and ought to look for extra assets through respectable industry and Government accomplices.
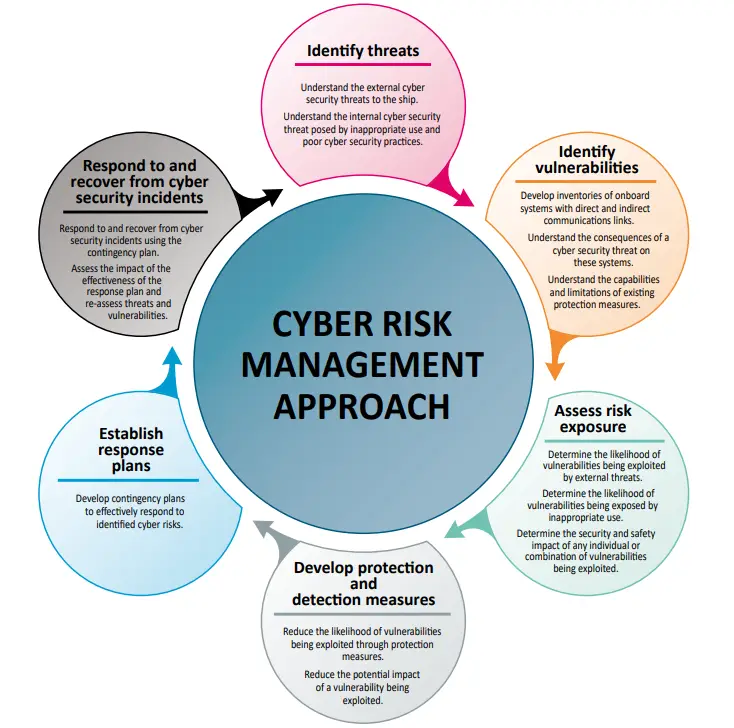
A few functional elements that support effective cyber risk management and these functional elements are of not sequential, and all should be concurrent and continuous in practice and should be incorporated appropriately in a risk management framework:
- Identify: Define personnel roles and responsibilities for cyber risk management and identify the systems, assets, data, and capabilities that, when disrupted, pose risks to ship operations.
- Protect: Implement risk control processes and measures, and contingency planning to protect against a cyber-event and ensure continuity of shipping operations.
- Detect: Develop and implement activities necessary to detect a cyber-event in a timely manner.
- Respond: Develop and implement activities and plans to provide resilience and to restore systems necessary for shipping operations or services impaired due to a cyber-event.
- Recover: Identify measures to back-up and restore cyber systems necessary for shipping operations impacted by a cyber-event.
Few Organizations to watch:
IAPH (International Association of ports and Harbors) – Founded in 1955, is a non-profit-making global alliance of 170 ports and 140 port-related organizations covering 90 countries. Its member ports handle more than 60 percent of global maritime trade and around 80 percent of world container traffic. IAPH has consultative NGO status with several United Nations agencies. In 2018, IAPH established the World Ports Sustainability Program (WPSP). WPSP covers five main areas of collaboration: energy transition, resilient infrastructure, safety and security, community outreach and governance.
ICHCA (International Cargo Handling Coordination Association) -Founded in 1952, is dedicated to improving the safety, security, sustainability, productivity and efficiency of cargo handling by all modes and through all phases of national and international supply chains. ICHCA International’s privileged NGO status enables it to represent its members and industry at large in front of national and international agencies and regulatory bodies including IMO. ICHCA’s International Technical Panel also provides technical advice and publications on a wide range of practical cargo handling issues.
Cyberattack scenarios at the port community level
- Acquiring critical data to steal high value cargo or allow illegal trafficking through a targeted attack.
- Propagation of ransomware leading to a total shutdown of port operations.
- Compromise of port community systems for manipulation or theft of data.
- Compromise of operational technology systems creating a major accident in port areas.
The Organizational ISSUE: To exacerbate the situation, implications will fill the vacuum made by the shortfall of normal definitions. For instance, when the term ‘cyber security’ emerges in the administration gatherings of numerous associations, non-technical leadership habitually highlight the “IT Person” as the de-facto individual answerable for dealing with the cyber risk. Such a response, and the practically visually impaired spread of this insight inside numerous associations and gatherings thereof, basically addresses a dismissal of aggregate liability. C-level administration could rather embrace by figuring out that digitalization and cyber security “are not IT issues, but rather business issues.” However, establishing a shared vocabulary is just the first step in creating a common language. The challenge remains to bridge the language barrier between technical and nontechnical leadership, with the latter group representing most port community stakeholders.
Asking yourself? What is lacking in Cyber defense of port security?
While the reasons for the lack of a community approach vary with each port, typical contributing factors include:
- Lack of a Port Community Policy
- Lack of Visibility
- Unwillingness to Share Cyber Information
- Lack of Resources
- Early Warning System
- Collaboration Forum
Case Study Example:
- The Port of Los Angeles Cyber Security Operations Center employs advanced technologies with layered detection capabilities. At the perimeter of the network, some 40 million unauthorized intrusion attempts are blocked every month. Within the network, multiple intrusion detection layers are used to continuously search for, detect and contain suspicious activities.
- The Port of Rotterdam Authority has developed its own cyber crisis response strategy which includes a Port Crisis Team. The aim of this team is to make strategic decisions on the continuation of safe and efficient handling of shipping. The Port Crisis Team is supported by three action centers. One focuses on maritime issues, another on solving the IT issue at hand and the final center aims to align communication (both inward and outward) between the parties involved.
Recent Scenario in India:
Mumbai Port under Ransomware attack: A suspected cyber-attack of the management information system (MIS) has vastly affected the container terminal run by the state-owned port authority at Jawaharlal Nehru Port which handles about 50% of the overall containerized cargo volume, across major ports in India, this incident was happened on February 21, 2022. This the same port that was under cyber attack in the year 2017 as well, as you see the more blind spotted Ness among the companies that handle the ports and government of India not taking proper measurements like the contingency plans for cyber threats and action response/ Incident response to happen this has been failed. As this port is handled by Danish shipping giant AP Moller-Maersk, which said that the cyber-attack had caused outages in its computer systems globally and couldn’t share proper details.
As these types of attacks will increase the load at other connected ports and without proper contingency plans, we can say it’s a clear “Critical Infrastructure Failure” by the government and by the shipping community which I personally hope they will resolve this at the earliest.
This is one of the key Industrial Control Security failure that a developing country like India, with huge population needs to address immediately as Nation wide threat actors are espying on the areas of vulnerabilities.
Published by – Sai Ram
Source:
https://www.iacs.org.uk/publications/recommendations/161-180/rec-166-new-corr2-cln/
https://www.ics-shipping.org/wp-content/uploads/2021/02/2021-Cyber-Security-Guidelines.pdf
Related Tags- cyberrisk, cyberattack, transportation, data, framework, cybertechnology, security, cybersecurity, sensordata, protect, detect, protection
